KeePassX Tutorial: Just the Basics
Introduction
This overview was originally part of my post on fixing shared password vulnerabilities but may be helpful to anyone interested in an overview of how password database software works. I’ll be focusing on one particular choice but toward the end I’ll list some popular alternatives.
KeePassX is a clone of the originally Windows-only KeePass software; this version is noteworthy for being compatible with KeePass databases, cross-platform, and open source. It’s also my personal choice and I can comment on it from that perspective. Like similar software and services, its purpose is to help the user maintain a secure and encrypted database of account credentials; it includes a powerful built-in password generator among other features. There are also mobile apps compatible with databases created with this software; see KeePassDroid for Android or MiniKeePass for iOS.
Importance of Open Source
There are a variety of viewpoints on the benefits or lack thereof of open source software (OSS). In the case of password management software or, more generally, any software you need to trust with your security and privacy, I argue that one should consider OSS before closed source alternatives — all other things being equal. OSS means that a piece of software can be audited by both the individual user and by the community as a whole; this makes inserting backdoors or purposefully weakening security impractical, because even if you don’t have the expertise to audit the source code the community generally will.
There was some recent controversy surrounding the NSA and Linux in which, in response to a question about whether the NSA had approached him to insert a backdoor into the Linux kernel, Linus Torvalds jokingly nodded yes while saying no. Some coverage took this as a direct confirmation that they had approached him but he later clarified that it had been meant as a joke. Later his father suggested that he had been approached after all although I didn’t interpret it in such a definitive manner myself. In either event it doesn’t matter since the Linux kernel’s source code is freely available for auditing and, given the expertise of the community of kernel developers, it is frequently audited. In short, backdooring Linux is impractical, and for the same reasons so is backdooring OSS security software like KeePassX.
Bottom line: OSS should be viewed as more trustworthy than otherwise equivalent closed source software.
Installation
Linux users will typically find this in their distribution’s repositories, and if that’s the case they should generally use that version unless there’s a good reason not to; in a terminal enter apt-get install keepassx (Debian, Ubuntu, and derivatives) or pacman -S keepassx (Arch and derivatives) or use your favorite GUI package manager. If KeePassX isn’t in the repos then download the KeePassX source code tarball and follow the instructions in the INSTALL file.
OS X and Windows users will find installers in the above link.
Using KeePassX
Here’s what the starting screen looks like before any password databases are created:
Go to File → New Database and you’ll arrive at:
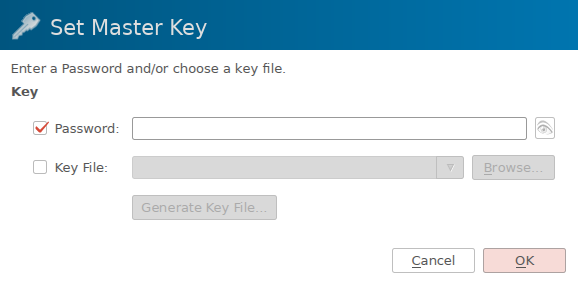
Here is where you should select a strong and unique password you can remember; this is the major security bottleneck with this scheme (but is mitigated by a number of factors) so it should be taken seriously. This should be a brand new and unique password — similar to LastPass’ branding, this is meant to be the last password (more or less) you’ll ever need to remember. Consider consulting my guide on creating strong memorable passwords.
As for the key file option, this increases security substantially although I feel it’s unnecessary for practical every-day security; basically in addition to a password you’ll need to be in possession of the key file to unlock the database. If you want to do this then generate the key file here, make it read-only with chmod 400 /path/to/keyfile or equivalent, and save it on two USB drives (don’t risk a single point of failure!). Optionally make the file immutable if the USB drive’s file system supports attributes with sudo chattr +i /path/to/keyfile. Note that if you make the file immutable and you want to move it or change it in any way, you’ll have to remove that attribute with sudo chattr -i /path/to/keyfile first.
Ok great, we have ourselves a password database so let’s start populating it with our credentials. Go to Entries → Add New Entry and you’ll arrive at:
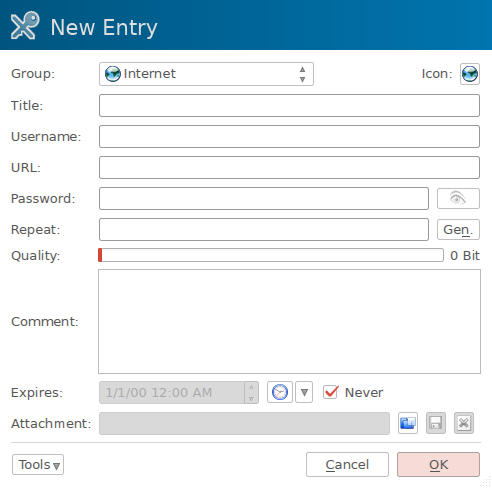
The fields are straightforward; at the very least enter a Title (for organizing your database), Username, and generate a Password (more on that in a moment). The URL is just for convenience and I like to use Comment for notes about things like recovery keys, presence of security questions (and if so which random security question an entry uses), and any other relevant information. When you’re ready, click Gen to create a password; you’ll be greeted with a screen like:
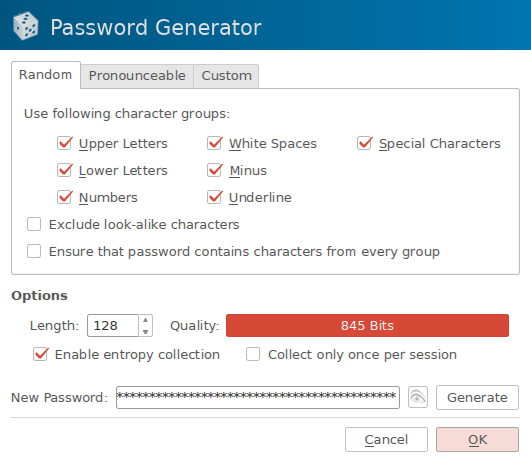
This is where you get to optimize the password for this particular account’s requirements; most of the time you have a specific maximum length to adhere to any specific characters that aren’t allowed (I’d go on about why these should never be as strict as they sometimes are… but that’s out of our control unfortunately). Select as many character groups as your password input prompt will allow and try to select the maximum length (if you’re using Firefox or Chrome try right-clicking on the password entry field and select Inspect Element to see if maxlength= is specified — that’s usually the same as their validation systems allow). Go ahead and enable entropy collection and select Generate:
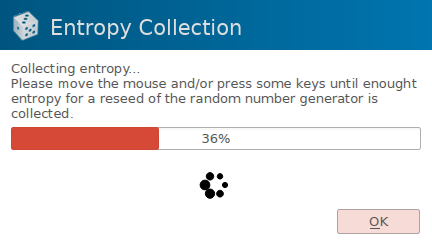
Follow the prompt’s instructions; try to be as random as possible and jitter your mouse sporadically until the process is finished and your password is created. Hit OK, File → Save Database for good measure, and input the new password in the form of interest. If it gives an error then change the length or character groups accordingly and regenerate it. Once you’ve added some accounts your database screen will look like this:
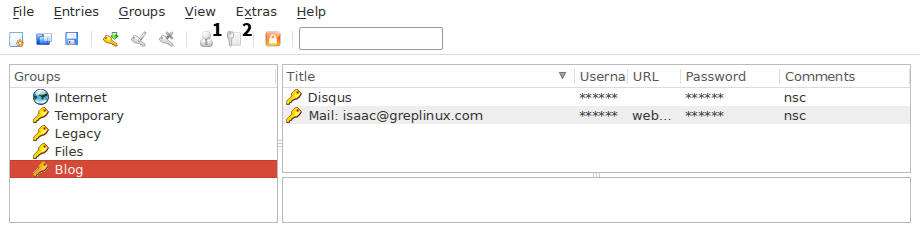
Icon 1 is used to copy a particular entry’s username to the clipboard while icon 2 is used to copy the password. Now you have a system that will let you log into any of your accounts by clicking just a few buttons and you’ve removed the burden of memorizing passwords almost entirely.
Alternatives to KeePassX
The way KeePassX works is similar to how other password databases (password managers) work. Take note of how KeePassX is open source, cross-platform, and offline-only; alternatives may differ in this regard. A quick Google search will turn up several alternative choices, but I’m going to very briefly highlight KeePass (as opposed to KeePassX) and LastPass which are both very popular and serve to illustrate some of these differences mentioned above.
KeePass
KeePass is an offline-only OSS password manager developed for Windows. There are unofficial ports using the Mono platform for Linux, Mac OS X, and mobile platforms. Take note that KeePassX databases are compatible with KeePass databases.
LastPass
LastPass is an online-only closed source password manager. The benefits of it being browser-based are convenience, inherent cross-platform capabilities, and not relying on the security of your local machine to secure your passwords. On the other hand it’s closed source so the platform’s security cannot be publicly audited; in spite of this there has only been one major vulnerability associated with it based on an XSS vulnerability, but there were no confirmed cases of credentials being compromised. Also, instead of being able to take the security of your local machine into your own hands you must again trust the LastPass team for this part of security. Ultimately we sometimes choose to sacrifice some amount of safety in exchange for some convenience and it’s up to the individual where the greatest value lies.