TrueCrypt Encryption Overview
Introduction
TrueCrypt is open source cross-platform encryption software that has enjoyed some very public success including stumping the FBI. It has also been the subject of debate on the authenticity of its security due to the lack of auditing of the source code by expert cryptographers although recent crowdfunded efforts seek to alleviate that. I propose TrueCrypt as a viable and sufficiently trustworthy (up to the point of reasonable paranoia) application with which to encrypt sensitive data such as password databases.
Beating the FBI: Operation Satyagraha
In 2010 it was revealed that the Brazilian National Institute of Criminology (INC) and the United Stated FBI spent almost a year failing to break encryption on hard drives encrypted with TrueCrypt belonging to banker Daniel Dantas. The majority of the time was spent using simple brute force dictionary attacks on the master password but one can assume they first exhausted more sophisticated approaches.
This was a well-circulated story that caught the eyes of many interested in security and encryption topics including myself. Looking a little deeper one discovers that TrueCrypt claims to offer a variety of strong encryption options including full-drive encryption, encrypted file containers, and plausible deniability encryption.
A Cautious Note: Unaudited Open Source Software
I’ve briefly written about how open source software improves trust and security since an entire community of interested individuals can audit the source code to ensure proper security and absence of backdoors or other malicious code. While TrueCrypt is open source software with its source code available for download, there are two notable caveats.
First, the development itself is a closed process; while the source code is published after a release, the development of the release itself happens behind closed doors. This isn’t itself dangerous so long as the source code is audited; however, and second, TrueCrypt is notable for not having been audited by cryptography experts.
There has recently been a crowdfunded effort to audit TrueCrypt which is underway so hopefully this will change before long. One should approach trust in software like the scientific community approaches trust in the results of a single publication: it’s all about peer review, and until there’s a community consensus that the source code is authentic one should be skeptical.
That all being said, I enjoy the use of TrueCrypt for a few reasons:
- I’m frankly not interesting enough to be the target of state-funded code breakers, and with high probability neither are you; TrueCrypt will still likely triumph over any ordinary attacker
- It’s cross-platform and easy to use
- In conjunction with techniques on memorizing strong passwords and password databases like KeePassX, one can achieve very usable, very strong online account credential management
Installation
With historical and cautionary notes out of the way, let’s get to actually using the software. Users of Windows, Mac OS X, and Linux will find installers. As an alternative, although it has been noted to be fairly challenging, adventurous users can compile TrueCrypt from its source code. Linux users will generally not find TrueCrypt in their repositories as several distributions have taken issue with its status as free and open source software, but at least Arch Linux users will find it in the [extra] repository: pacman -S truecrypt.
Creating a New Volume
When you launch TrueCrypt you’ll initially be greeted with this screen:
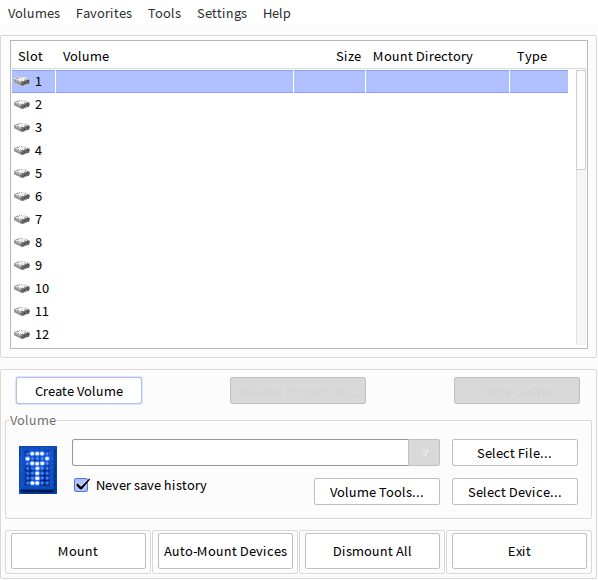
To get started, select Create Volume and you’ll be given the following choice:
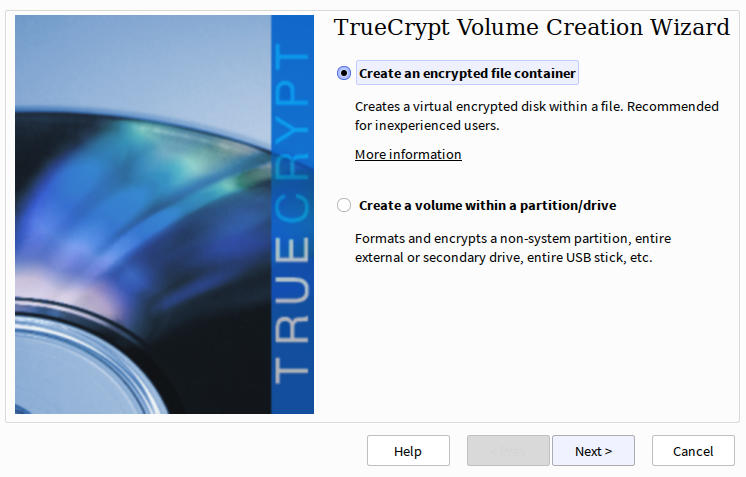
For now go ahead and create a file container; encrypted drives and partitions will be discussed later.
Encrypted File Containers
TrueCrypt can make an encrypted file container on your drive. What this does is create a container file with size equal to the desired storage space that is strongly encrypted by a password and/or keyfiles. TrueCrypt volumes can be either standard (just as described before) or hidden (employs plausible deniability methods). Both options will be covered.
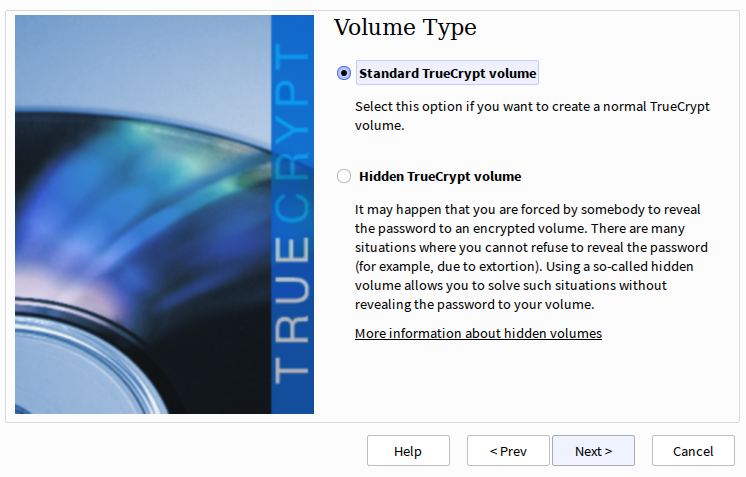
Now choose between a standard and hidden TrueCrypt volume. Here’s a rundown of the differences between the two.
- Standard TrueCrypt Volume: These are simple file containers guarded by a single password. If one enters the incorrect password they can’t decrypt the container and access its contents, while if they enter the correct password they’ll have access to the files.
- Hidden TrueCrypt Volume: These volumes employ plausible deniability encryption, which is to say there are two volumes: an outer volume with innocuous contents that can be believed to be the actual safeguarded contents and an inner hidden volume with the actual contents one wants to safeguard; each volume has a separate password. The idea is that one can provide the outer volume’s password if a third party attempts to force one into divulging the password; the attacker will unlock the innocuous contents while the important contents remain safe. If interested in making a hidden volume please read the documentation (the link in bold) in order to learn how to properly protect a hidden volume outside of the creation process; there are a few considerations.
The instructions for both cases are similar except for a few differences I’ll make note of. In principle I prefer plausible deniability methods although the fact that I’m publishing this effectively nullifies their use for me; neither is more convenient to use in practice. If you chose to create a hidden TrueCrypt volume the following set of instructions apply to both the outer (unimportant) and inner (hidden, important) volumes.
In the next screen select the volume location; you’ll probably want to create a new file so enter its name at the desired location. Now choose the desired encryption options:
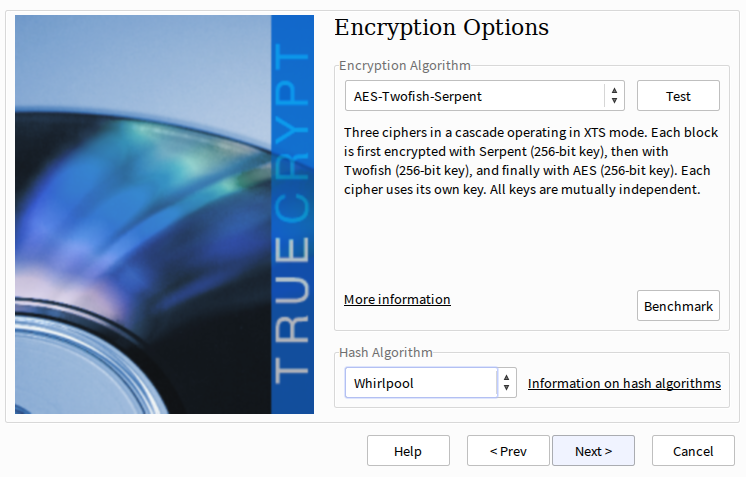
Here you’re provided links for technical information on the different algorithm choices before making a selection. Pending any disclosures of vulnerabilities, I prefer the three-cipher options for the encryption algorithm (AES-Twofish-Serpent or reverse) and Whirlpool for the hash algorithm; I recommend reading the documentation and making an informed decision.
Next you select the volume size; TrueCrypt will inform you of the maximum size based on the location of the container you selected. Note: if you’re creating a hidden TrueCrypt volume you need to allocate enough space for both the outer volume and the inner hidden volume.
Now you have to select the password and/or keyfiles. If you choose to use a keyfile you have a variety of options including using an existing file or generating a new one. If you do choose this route, be sure to keep at least two copies of the file and store them in such a way that they won’t be modified, otherwise if altered they’ll be rendered useless and you’ll lose access to your container; they should also be stored with other miscellaneous files to obscure their actual use. For every day use I personally prefer selecting a strong password alone since it’s easier to manage, but remember that your encryption is only as strong as your password and/or keyfiles. The FBI and INC would have trivially broken their target’s encryption if a weak password was used.
Note: At this point if you chose to create a hidden TrueCrypt volume you’ll be prompted to seed the random pool; see after the next paragraph for details on that. Then you’ll be able to open the outer volume and place seemingly sensitive files that you don’t care about inside of it, and you should do so. Once that is done you’ll repeat the above steps for the inner (hidden) volume.
Next you’ll select the formatting options. FAT filesystems can be considered universally compatible between modern operating systems, but you may have other preferences depending on your needs. Once selected you’ll be presented with an entropy collection screen:
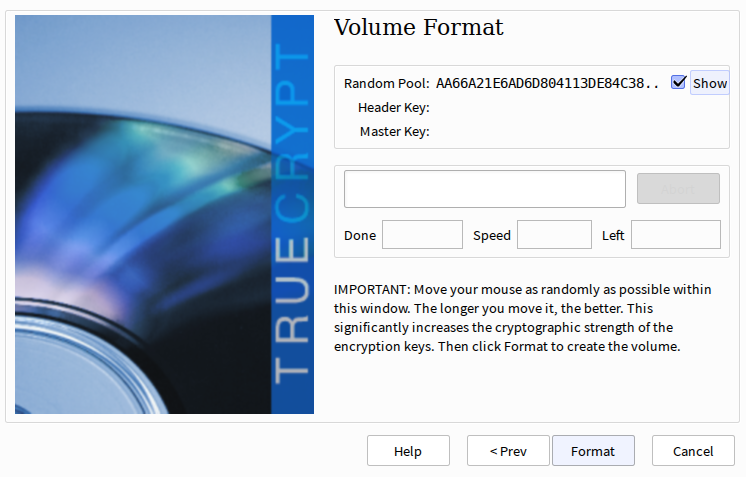
Here you should jitter your mouse sporadically for some time (about a minute is probably good); this strengthens the cryptographic entropy pool used to generate random numbers for key generation. When ready, select Format and you’re done!
Returning to the main screen you can now select an empty slot to use to mount your file container. Choose Select File and locate the container you just created and select Mount. Enter its password and/or supply keyfiles and your file container will be mounted and ready to store sensitive files. Once you’re done, close any programs using those files and then dismount the container from the main TrueCrypt screen.
Encrypted Partitions or Drives
Instead of creating an encrypted file container where you can store sensitive data, TrueCrypt can also encrypt entire drives or partitions in drives. When you select Create Volume from the main screen there is also an option to create a volume within a partition or drive; if you select this you’ll choose between standard and hidden TrueCrypt volumes as before and then you’ll be able to select the device:
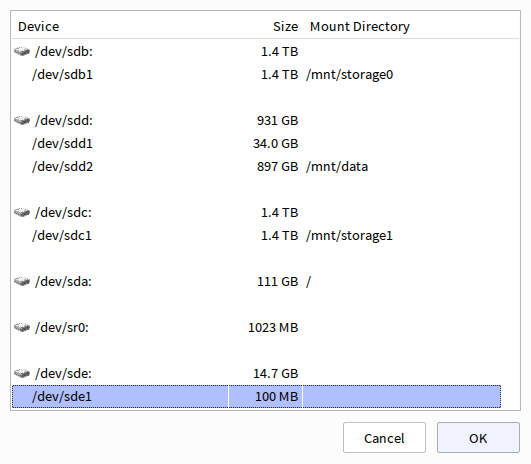
Here you’ll need to very carefully select the intended device to make sure you don’t wipe important data on accident. In this example I have selected a small partition on a USB flash drive; entire drives may also be selected. Once you’ve made your selection the steps are the same as for creating an encrypted file container. When you’re finished encrypting the device and want to mount it, this time you’ll select the appropriate device instead of a file.
Concluding Remarks
Once you’ve done this once or twice it becomes a fluid process to create these volumes. One of the major practical uses of TrueCrypt encryption is as a safe way to store sensitive files in cloud services like Dropbox. For instance, one could create a KeePassX password database, which is already secured by what should be a strong password and/or keyfiles, and store that in a hidden volume inside a small TrueCrypt encrypted file container. This container can then be placed in Dropbox or another cloud storage service; even if it was seized in an attack it would be very, very challenging for a remote thief to recover the password database. I provide a thorough look into how to set up and manage this secure syncing.
Encrypting one’s entire life may be more trouble than it’s worth for the vast majority of us, but encrypting small critical pieces of it isn’t much of a hassle compared to the benefit.